
The Importance of Studying and Testing Electrical Parts
When we think of electronics, we often imagine the sleek design of a smartphone or the sophisticated software of a

When we think of electronics, we often imagine the sleek design of a smartphone or the sophisticated software of a

Access control is an essential aspect of premises security. It allows authorized individuals access while keeping unauthorized persons out of

Turbochargers, also known as forced induction systems, are crucial components in today’s high-performance engines. These devices efficiently boost an engine’s
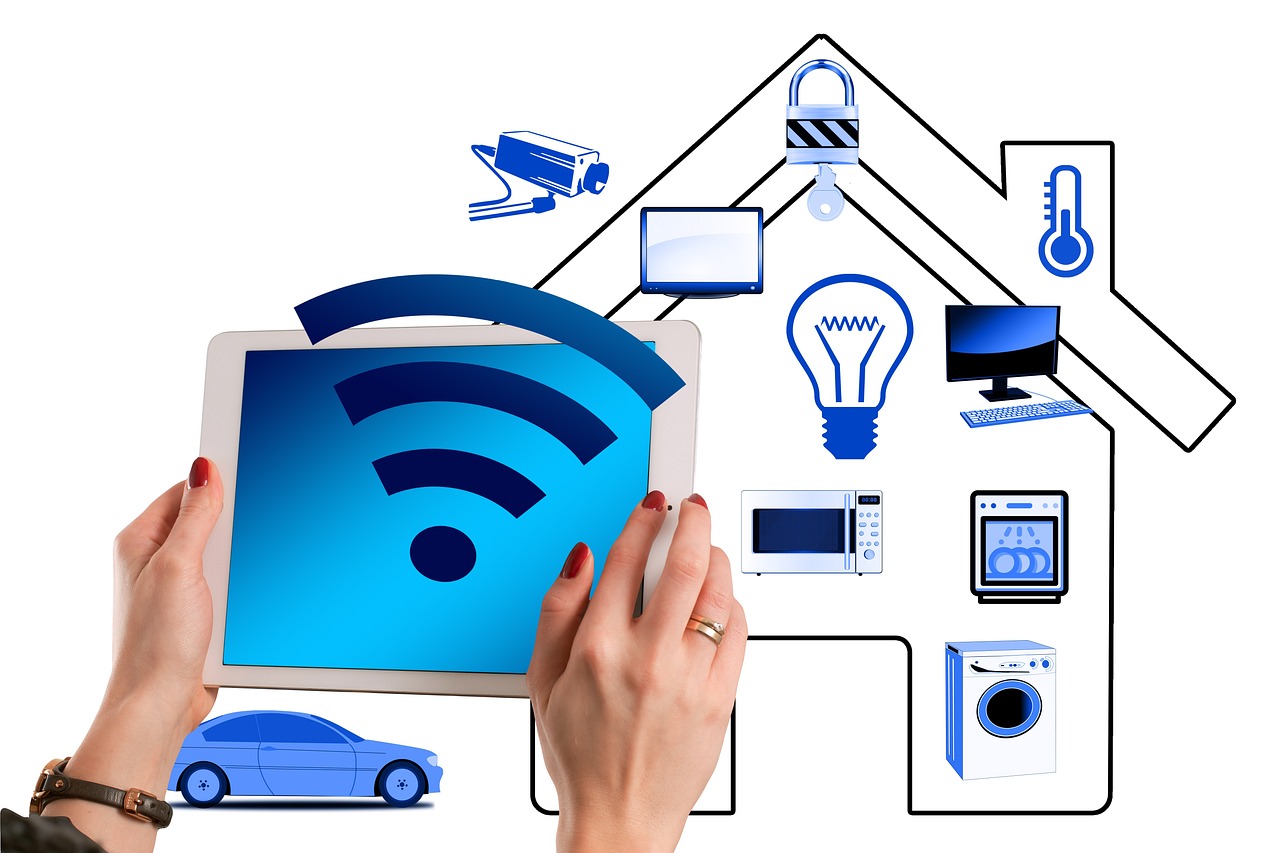
As technology continues to advance, so does its integration into our homes. One example of this is Veego – a

Virtual Reality VR is the latest technology that has taken over London’s entertainment industry, and it’s revolutionizing how people experience

Digital twin software is a rapidly growing technology that is changing the way industries operate. Digital twin technology creates a

Getting an expert opinion has never been easier thanks to the internet. If you have a question about a particular

As the world moves towards faster and more advanced technology, Australia is not one to be left behind. 5G technology

Are you tired of managing all the devices in your home separately? Do you want to streamline your home automation

Artificial intelligence AI technology is taking over the world. It is changing how we live, work, and interact with one
Copyright © 2025 | Powered by Beboh.net
Copyright © 2025 | Powered by Beboh.net